with typical American extravagance, they have two of them
Galli [comrade/them]
- 0 Posts
- 7 Comments

 41·7 months ago
41·7 months agoI can excuse attempting to compromise millions of computer systems worldwide for nefarious purposes but I draw the line at violating the contributor guidelines of an opensource project.

 51·7 months ago
51·7 months ago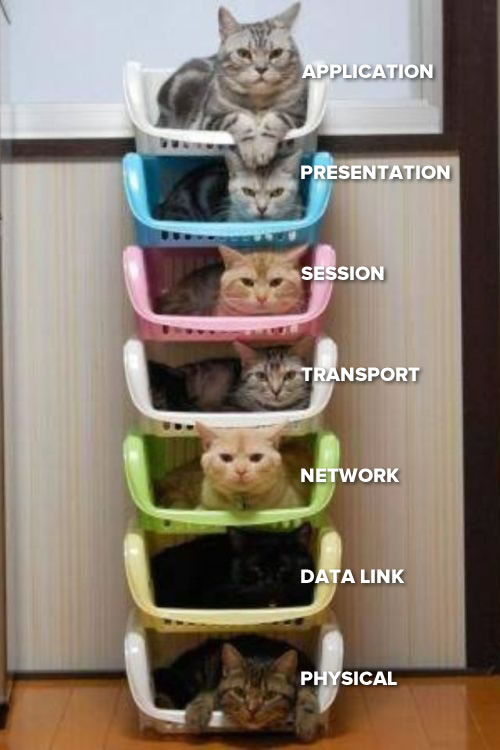
The top cat uses ports to sort messages based on application.

Think pigeon holes, applications usually use protocols which are assigned a number by convention. The application gets it’s message out of it’s assigned ports instead of having to sort through all the messages.

 5·10 months ago
5·10 months agoVoter registration is public information and sufficient for cold callers.
If you live independently you will inevitably have to make privacy sacrifices for the sake of expediency. Having a bank account is probably going to be one of them. There are many essential services that you use but probably do not think of as an eighteen year old that may share information when you provide for yourself such as your phone carrier, ISP, utilities such as power, water, gas etc, insurance, health services, education or certification providers, employment or recruitment agencies, the list just goes on and you will have to thoroughly evaluate every company you interact with and in many cases there will simply be no realistic privacy respecting option.
Keep fighting to protect your privacy but don’t put an impossible burden on yourself to be perfect. You will make mistakes, you will make compromises, you will probably get spam. Welcome to late stage capitalism.

 83·11 months ago
83·11 months agoalias?

 2·11 months ago
2·11 months agoThey don’t want pirates removing the slot machine monetization from their game for children.

“if” gcc had a Ken Thompson hack how do you secure checks notes anything